Real-Time Insights, Continuous Compliance
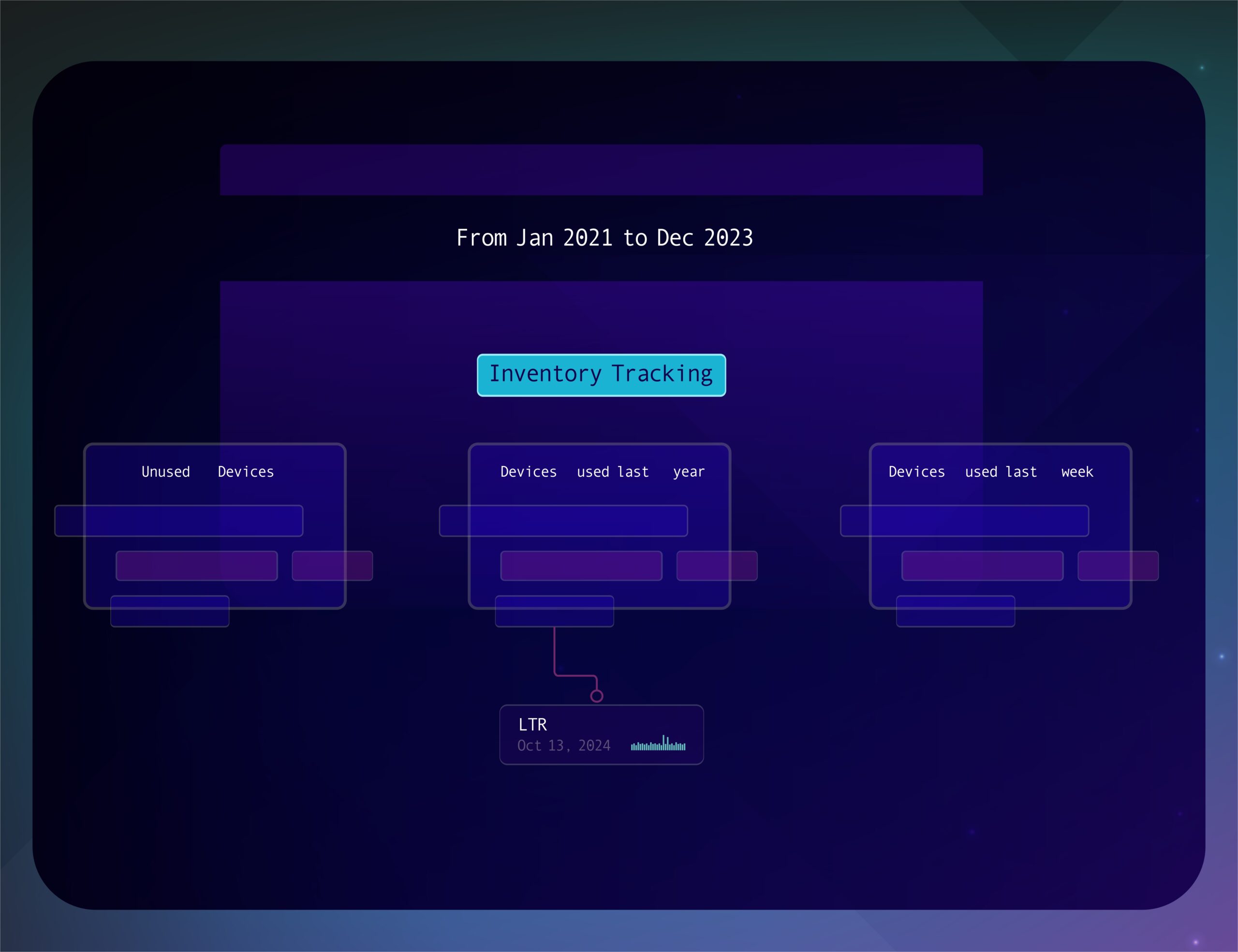
Virtual CMDB
Build a comprehensive virtual CMDB for real-time insights into coverage gaps and security vulnerabilities. Aid your existing CMDB with real time insights from your data.
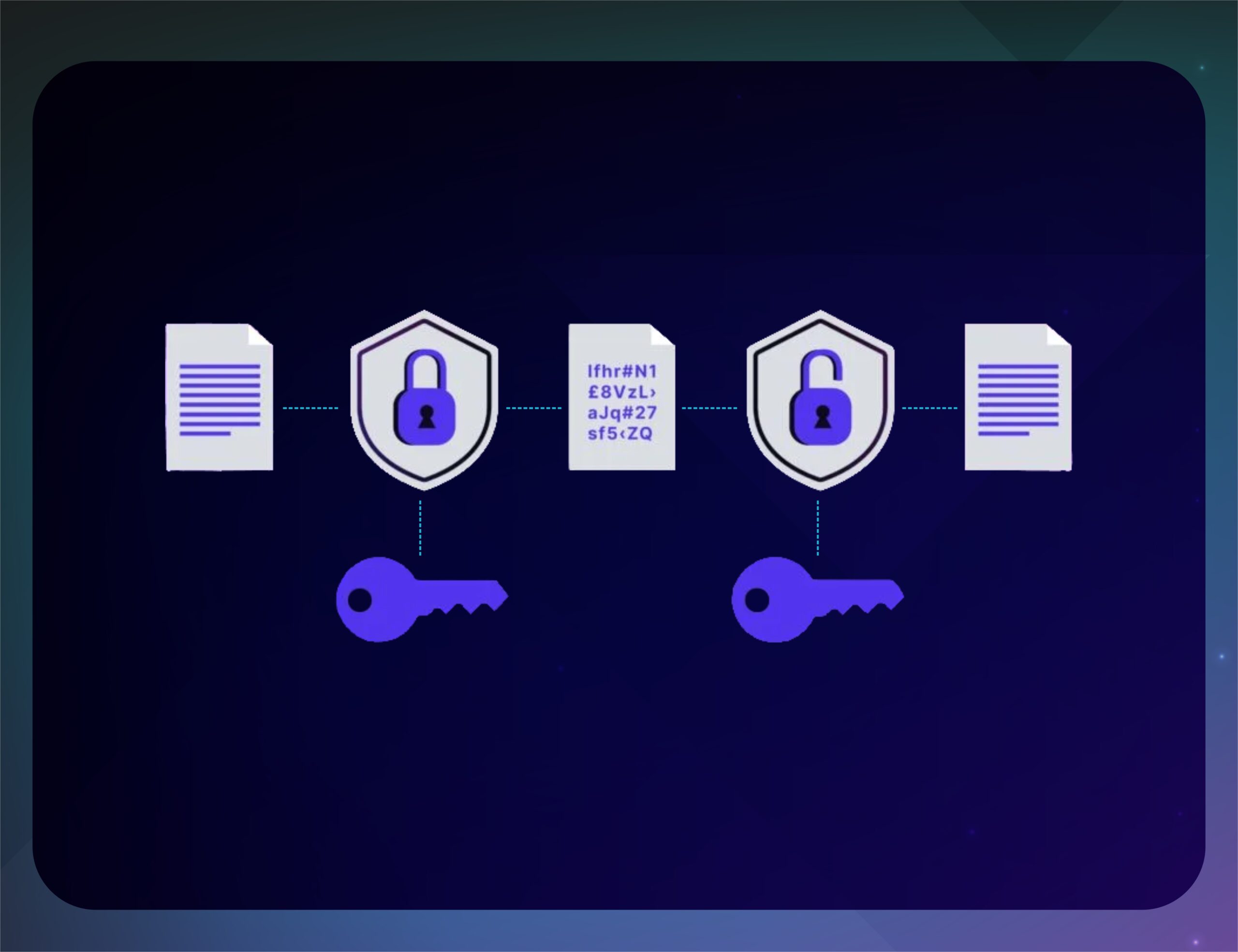
Sensitive Data Detection
Detect and classify sensitive data patterns to ensure data protection and compliance. Quarantine, mask, redact, and drop sensitive data, to avoid sensitive data proliferation.
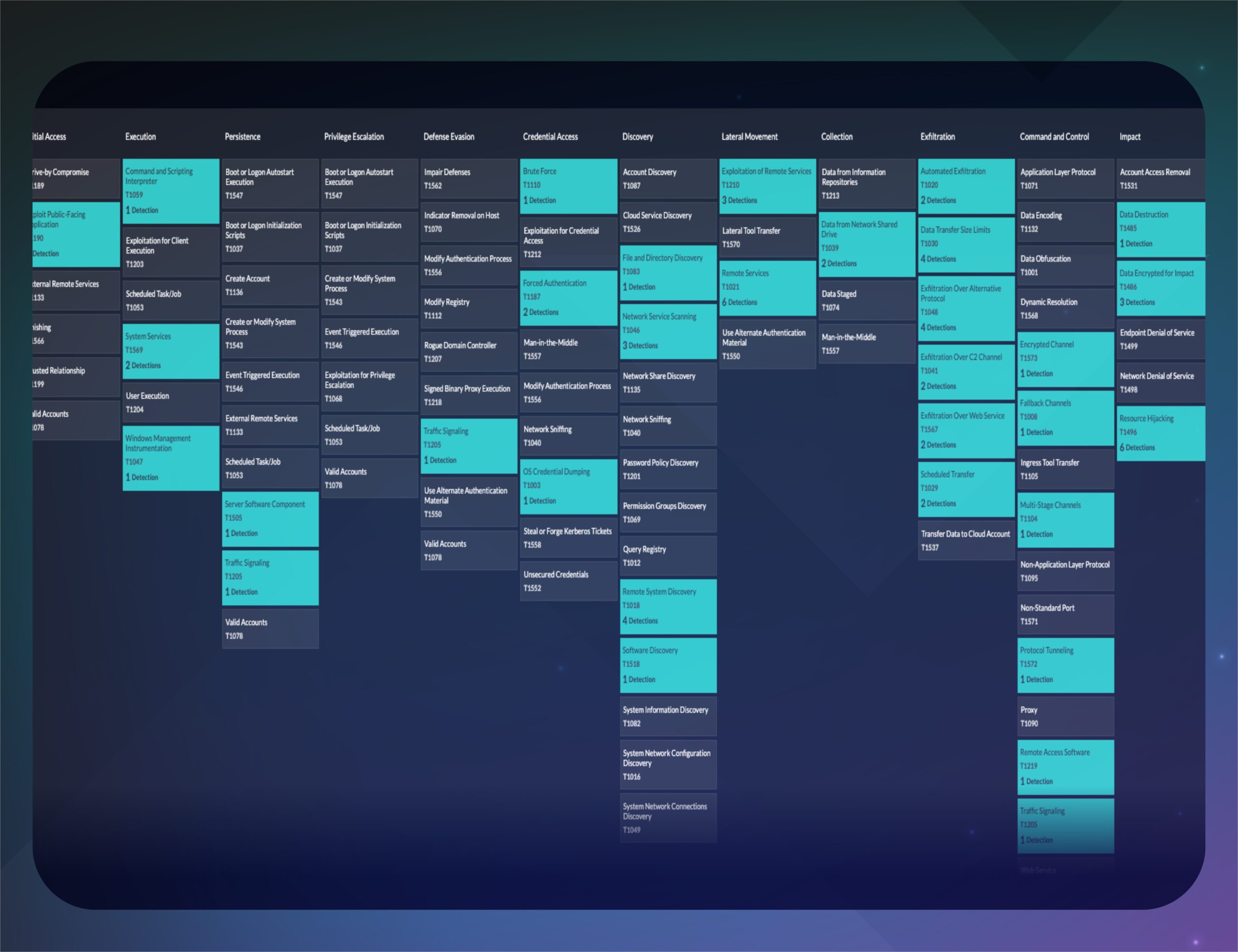
Posture Management
Identify telemetry coverage gaps and provide guided recommendations based on industry frameworks like MITRE and NIST. Map processed data to identify security gaps and vulnerabilities, enabling proactive risk mitigation.
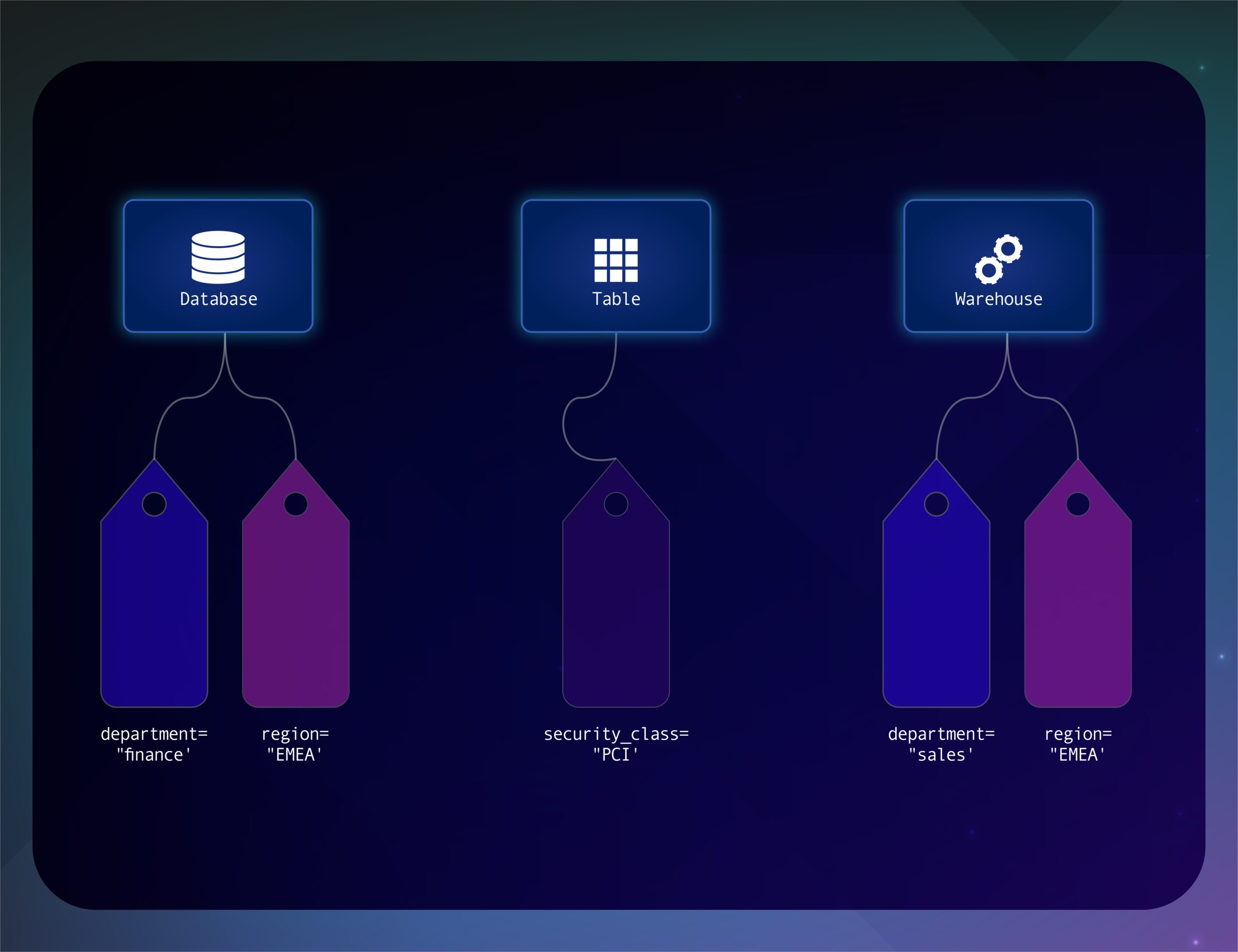
Asset Tagging
Tag critical assets and ensure continuous compliance with regulatory requirements and security standards. Review Data flowing in & out of your critical assets and ensure conformance to security standards.
Discover how Databahn transforms your security incident mitigation and elevates threat-hunting efficiency, and improvement in speed, precision, and effectiveness.
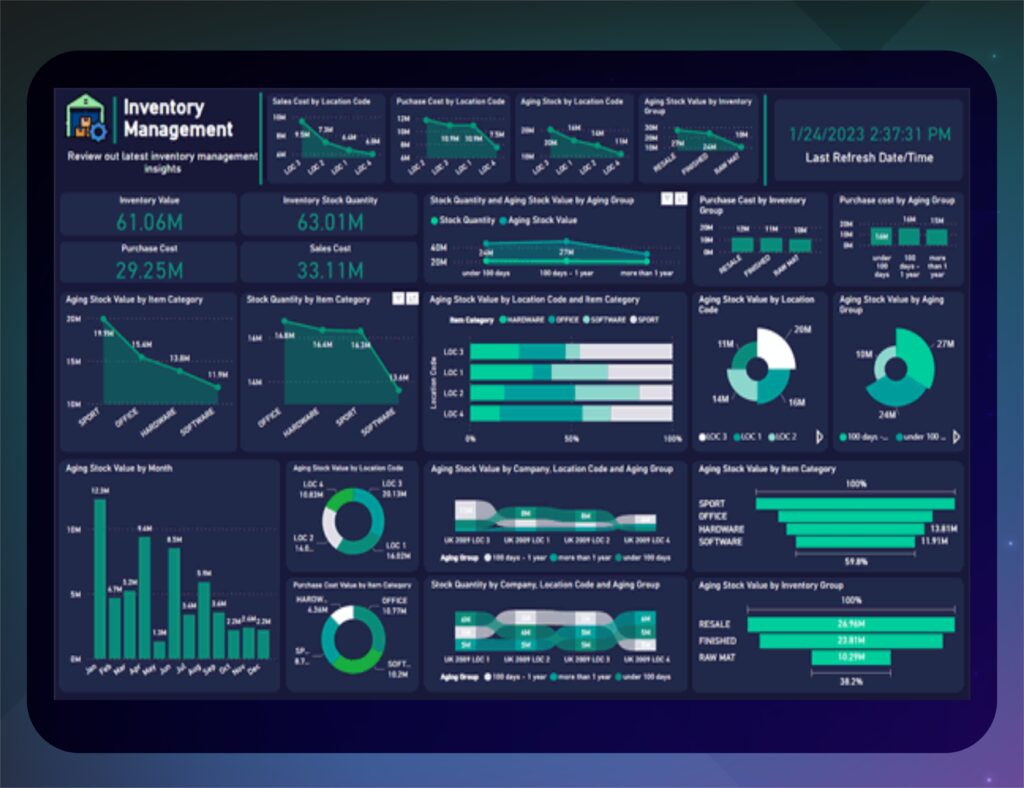
Complement your asset inventory with insights from your ecosystem. Identify coverage profiles, security standards compliance, etc. Identify rogue devices, review risk broken down by subnets, clean up asset tags for conformance, and keep your inventory up-to-date.
Tag your assets and monitor conformance to your regulatory and compliance needs. Look beyond point in time reports and provide a detailed continuous compliance view of your critical assets.


Detect occurrences of sensitive PII data, passwords in clear texts, GDPR Violations etc. and define your own data tags. Avoid sensitive data proliferation by having a single data command center.
Gain real-time visibility into security posture gaps and vulnerabilities, enabling proactive risk management. Insights from your environment real time to tell you the security profile of every single asset in your ecosystem



















